May 2024 M T W T F S S 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 Categories
- General (35)
- Enterprise Library (2)
- Entity Framework (1)
- File Systems (1)
- Hyper-V (4)
- IIS (2)
- Visual Studio (2)
- SAP (5)
- Silverlight (23)
- SQL (13)
- Web Service (9)
- WCF (5)
- General (35)
Category Cloud
Archives
- Follow Unsal Donmez on WordPress.com
Close Code Analysis on VS 2013
– Open Microsoft.CodeAnalysis.Targets notepad %programfiles(x86)%\MSBuild\Microsoft\VisualStudio\v12.0\CodeAnalysis
– Find RunCodeAnalysisOnThisProject and false the value as shown below.
<RunCodeAnalysisOnThisProject>false</RunCodeAnalysisOnThisProject>
Posted in Visual Studio
Leave a comment
Sysprep – Fatal error occurred while trying to sysprep the machine
Setting HKEY_LOCAL_MACHINE\SYSTEM\Setup\Status\SysprepStatus to 7
Setting HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\SkipRearm to 1
Renaming (or deleting) C:\Windows\System32\sysprep\Panther
Make sure to do all three each time you attempt a sysprep.
Posted in Hyper-V
Leave a comment
Error message “The Computer Restarted unexpectedly or encountered an unexpected error” after System Startup on Windows 7 Recovery
1) On the same error screen press SHIFT+F10 and it will open up a black Window. (a command prompt window)
2) In the black windows type the word “regedit”(without the inverted commas and hit enter. That will open the registry editor.
In the Registry Editor..
Browse to….
HKLocal machine/SYSTEM/SETUP/STATUS/ChildCompletion, and after highliting childcompletion,on the right hand side check for setup.exe. if the value is 1 change it to 3
Posted in Hyper-V
Leave a comment
SQL Drop tables (mistaken) from master db
When I deploy the scripts to SQL server I have have a error and deployment was failed. All tables were created to master db and I wrote below script to remove all of them.
Uncomment to execute; –EXEC sp_executesql @str
DECLARE @str NVARCHAR(MAX)
SET @str = ”
/****DROP FOREIGN KEYS***/
WHILE ( EXISTS ( SELECT 1
FROM INFORMATION_SCHEMA.TABLE_CONSTRAINTS
WHERE CONSTRAINT_TYPE = ‘FOREIGN KEY’
AND table_catalog = ‘master’
AND Table_name NOT IN ( ‘MSreplication_options’,
‘spt_fallback_db’,
‘spt_fallback_dev’,
‘spt_fallback_usg’,
‘spt_monitor’, ‘spt_values’ ) ) )
BEGIN
DECLARE @sql NVARCHAR(2000)
SELECT TOP 1
@sql = ( ‘ALTER TABLE ‘ + TABLE_SCHEMA + ‘.[‘ + TABLE_NAME
+ ‘] DROP CONSTRAINT [‘ + CONSTRAINT_NAME + ‘]’ )
FROM information_schema.table_constraints
WHERE CONSTRAINT_TYPE = ‘FOREIGN KEY’
EXEC (@sql)
END
/*******/
SELECT table_name ,
ROW_NUMBER() OVER ( ORDER BY table_name ) AS Rn
INTO #tempTable
FROM master.information_schema.tables
WHERE Table_name NOT IN ( ‘MSreplication_options’, ‘spt_fallback_db’,
‘spt_fallback_dev’, ‘spt_fallback_usg’,
‘spt_monitor’, ‘spt_values’ )
DECLARE @COunt INT
SET @COunt = 0 ;
SELECT @COunt = COUNT(*)
FROM #tempTable
DECLARE @TableName VARCHAR(50)
WHILE @COunt > 0
BEGIN
SELECT @TableName = table_name
FROM #tempTable
WHERE Rn = @COunt
SET @str = ‘Drop Table ‘ + @TableName + ‘;’
PRINT @str
–now to drop table uncomment below line
–EXEC sp_executesql @str
SET @COunt = @COunt – 1 ;
END
/*DROP temp DB*/
DROP TABLE #tempTable
Posted in SQL
Leave a comment
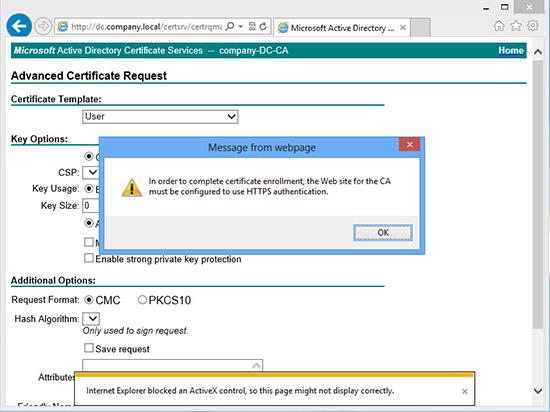
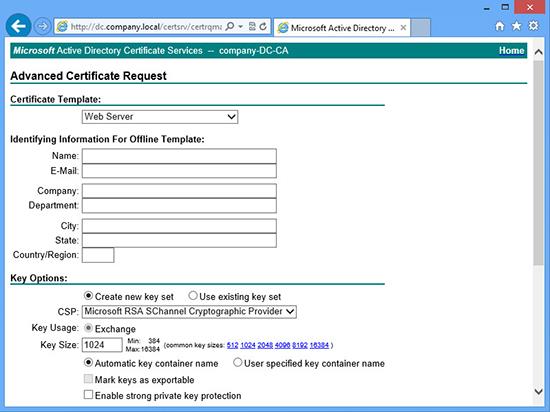
Certification Authority to use HTTPS authentication
Error.
In order to complete certificate enrolment, the Web site for the CA must be configured to use HTTPS authentication
Solution
The correct fix is to set the web server (IIS) to serve the certificate website securely using https, though you can just set Internet explorer to ‘work’ from your client machine if you are in a hurry.
Make Internet Explorer Work without Error
Note: This would need to be done on every machine that you wanted to access the Certificate Services web portal from.
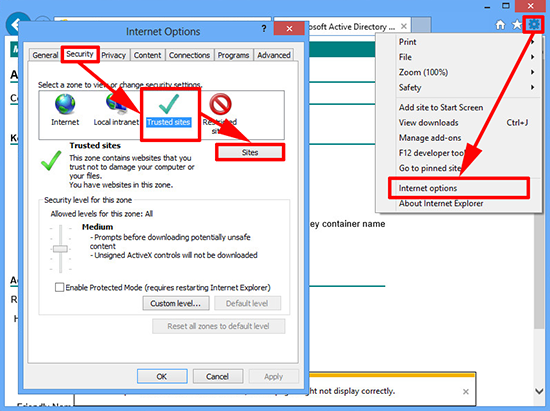
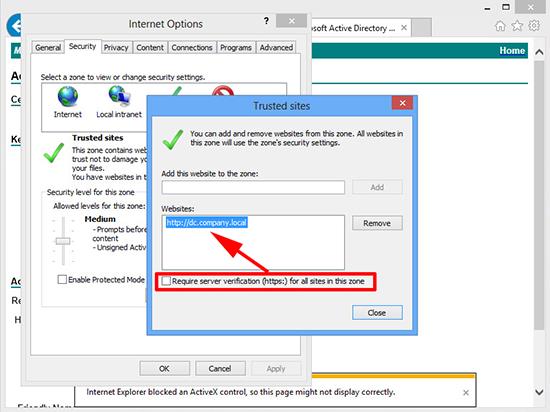
1. From within Internet Explorer > Internet Options > Security > Trusted Sites > Sites.
2. Untick ‘Require server verification (https:) for all sites in this zone’ > Then add in the URLof the CA > Close.
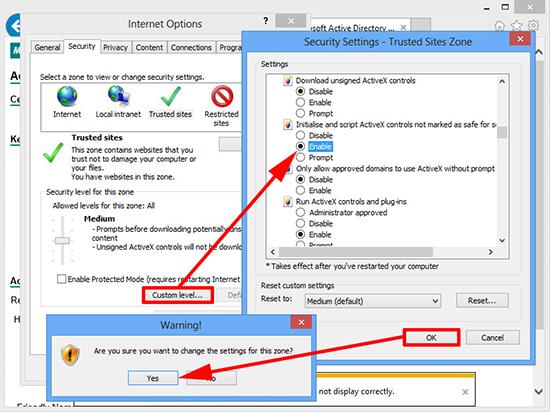
3. With Trusted sites still selected > Custom level > ‘Initialize and script ActiveX controls not marked as safe for scripting’ > Enable > OK > Yes.
4. Restart the browser and try again.
Set IIS to serve Certificate Services Securely (via https).
This assumes you have your CA and the web portal installed correctly.
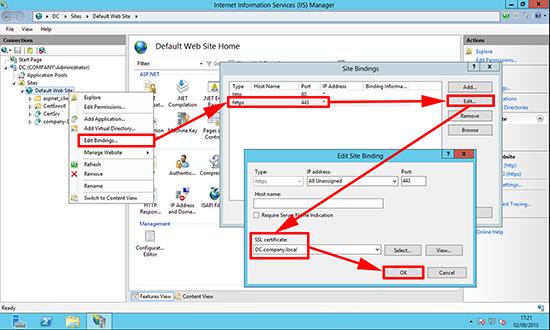
1. On the Certificate Services Server > Launch IIS Manager > Expand {server-name} > Sites > Default Web Site > Right Click > Edit Bindings > https > Edit > Select the self-signed server certificate [NOT the CA ONE] > OK.
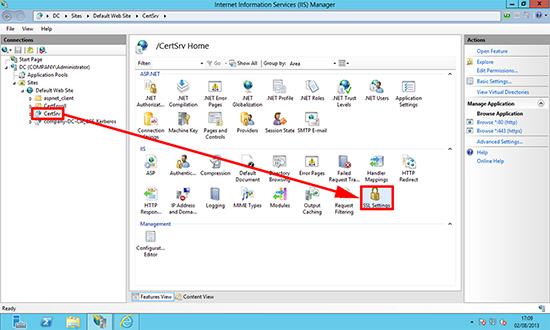
2. Expand Default Web Site > Certsrv > SSL Settings.
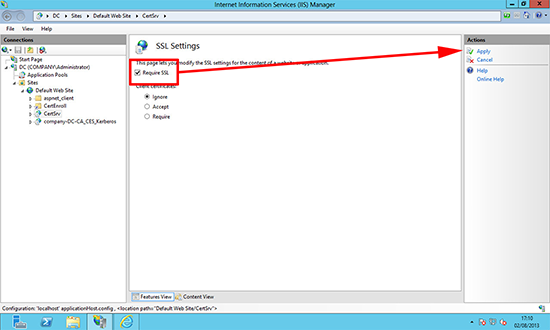
3. Tick ‘Require SSL’ > Apply.
4. That should be all you need, if it does not take effect straight away then drop to command line and run iisreset /noforce.
Posted in General
Leave a comment
Microsoft.SqlServer.Configuration.Sco.ScoException: The specified driver is invalid.
If you get the error below in the Detail.txt (100/Setup Bootstrap/Log.. ) when you installing the SQL Server ;
(To workaround the issue you need to temporarily match the user and system locales before setting up SQL server. In the scenario described in this article you need to set the User locale to your language so that it matches the System locale. After the setup is complete you can revert the regional settings back to desired configuration.)
Please run that command : C:\WINDOWS\SYSTEM32>Lodctr /R
If you have still got an error please check *.ini files in the InstallationMedia. There may be some encoding problems like japanese charecters etc.
Detail.txt
The configuration failure category of current exception is ConfigurationFailure
2013-11-29 17:29:00 Slp: Configuration action failed for feature SQL_Engine_Core_Inst during timing ConfigNonRC and scenario ConfigNonRC.
2013-11-29 17:29:00 Slp: Microsoft.SqlServer.Configuration.Sco.ScoException: The specified driver is invalid.
2013-11-29 17:29:00 Slp: ---> System.ComponentModel.Win32Exception: The specified driver is invalid.
2013-11-29 17:29:00 Slp: at Microsoft.SqlServer.Configuration.Sco.PerformanceCounter.LoadPerformanceCounter(String symbolInstallPath, String counterPrefixServiceName)
2013-11-29 17:29:00 Slp: at Microsoft.SqlServer.Configuration.Sco.PerformanceCounter.RegisterPerformanceCounterCore(String libraryFileName, String openFunction, String collectionFunction, String closeFunction, String symbolInstallPath, String counterPrefixServiceName)
2013-11-29 17:29:00 Slp: at Microsoft.SqlServer.Configuration.Sco.PerformanceCounter.RegisterPerformanceCounter(String libraryFileName, String openFunction, String collectionFunction, String closeFunction, String symbolInstallPath, String counterPrefixServiceName)
2013-11-29 17:29:00 Slp: --- End of inner exception stack trace ---
2013-11-29 17:29:00 Slp: at Microsoft.SqlServer.Configuration.Sco.PerformanceCounter.RegisterPerformanceCounter(String libraryFileName, String openFunction, String collectionFunction, String closeFunction, String symbolInstallPath, String counterPrefixServiceName)
2013-11-29 17:29:00 Slp: at Microsoft.SqlServer.Configuration.SqlEngine.PerfmonRegistration.RegisterCtrs(Boolean forceCopy)
2013-11-29 17:29:00 Slp: at Microsoft.SqlServer.Configuration.SqlEngine.SqlEngineSetupPrivate.Install_ConfigNonRC_Prepare(EffectiveProperties properties)
2013-11-29 17:29:00 Slp: at Microsoft.SqlServer.Configuration.SqlEngine.SqlEngineSetupPrivate.Install(ConfigActionTiming timing, Dictionary`2 actionData, PublicConfigurationBase spcb)
2013-11-29 17:29:00 Slp: at Microsoft.SqlServer.Configuration.SqlConfigBase.SlpConfigAction.ExecuteAction(String actionId)
2013-11-29 17:29:00 Slp: at Microsoft.SqlServer.Configuration.SqlConfigBase.SlpConfigAction.Execute(String actionId, TextWriter errorStream)
2013-11-29 17:29:00 Slp: Exception: Microsoft.SqlServer.Configuration.Sco.ScoException.
2013-11-29 17:29:00 Slp: Source: Microsoft.SqlServer.Configuration.Sco.
2013-11-29 17:29:00 Slp: Message: The specified driver is invalid.
2013-11-29 17:29:00 Slp: .Inner exception:
2013-11-29 17:29:00 Slp: Exception: System.ComponentModel.Win32Exception.
2013-11-29 17:29:00 Slp: Source: Microsoft.SqlServer.Configuration.Sco.
2013-11-29 17:29:00 Slp: Message: The specified driver is invalid.
2013-11-29 17:29:00 Slp: .Error: Action "SqlEngineConfigAction_install_confignonrc_Cpu64" failed during execution.
2013-11-29 17:29:00 Slp: Completed Action: SqlEngineConfigAction_install_confignonrc_Cpu64, returned False
2013-11-29 17:29:00 Slp: Sco: Attempting to get instance feature flag UpgradeIncomplete for feature SQL_Engine_Core_Inst, instance MSSQL10_50.MSSQLSERVER, machine name AIRSQL
2013-11-29 17:29:00 Slp: Sco: Attempting to create base registry key HKEY_LOCAL_MACHINE, machine AIRSQL
2013-11-29 17:29:00 Slp: Sco: Attempting to open registry subkey
2013-11-29 17:29:00 Slp: Sco: Attempting to open registry subkey SOFTWARE\Microsoft\Microsoft SQL Server\MSSQL10_50.MSSQLSERVER\UpgradeIncompleteState
2013-11-29 17:29:00 Slp: Sco: Attempting to get registry value SQL_Engine_Core_Inst
2013-11-29 17:29:00 Slp: Sco: Attempting to get feature configuration state for feature SQL_Engine_Core_Inst, instance MSSQL10_50.MSSQLSERVER
2013-11-29 17:29:00 Slp: Sco: Attempting to get instance feature flag ConfigurationState for feature SQL_Engine_Core_Inst, instance MSSQL10_50.MSSQLSERVER, machine name AIRSQL
2013-11-29 17:29:00 Slp: Sco: Attempting to create base registry key HKEY_LOCAL_MACHINE, machine AIRSQL
2013-11-29 17:29:00 Slp: Sco: Attempting to open registry subkey
2013-11-29 17:29:00 Slp: Sco: Attempting to open registry subkey SOFTWARE\Microsoft\Microsoft SQL Server\MSSQL10_50.MSSQLSERVER\ConfigurationState
2013-11-29 17:29:00 Slp: Sco: Attempting to get registry value SQL_Engine_Core_Inst
Posted in SQL
Leave a comment
Recovery policy configured for this system contains invalid recovery certificate
The Recovery policy configured for this system contains invalid recovery certificate message is known to appear when trying to encrypt a file or a folder using the Windows Encrypting File System. The File Recovery certificate being outdated or expired is the most frequent cause of this invalid recovery certificate message.
The message is shown in the following print screen:
Message about invalid recovery certificate shown after trying to encrypt a file.
When do I get the invalid recovery certificate message?
We already mentioned that the invalid recovery certificate message appears when trying to encrypt a file or folder using the Windows Encrypting File System mechanism. You can encrypt a file or folder in Windows by right clicking a file or folder in your Windows Explorer, entering the Properties screen and going to the Advanced options on the General tab. When you click check the “Encrypt contents to protect data” and hit Apply, you might encounter the Recovery policy configured for this system contains invalid recovery certificate message if your system is not set up the way it needs to be.
Why the invalid recovery certificate message appears?
When you enable encryption on a file or folder, Windows checks your file recovery certificate to see whether it is current and valid. This certificate is your help of last resort in the event when you need to recover encrypted files when the encryption key is lost or damaged. It is obvious that this message can show up “out of the blue sky” leaving the user helpless and wondering – at the moment when the certificate expires.
Security note:
On one hand, Windows does a good thing by checking the recovery certificate to help avoid situations when the data is lost for ever just because the encryption key is lost, but on the other hand, it is necessary to say that the recovery certificate is sort of a back door and as such can be exploited.
How to fix the Recovery policy configured for this system contains invalid recovery certificate message?
Fixing your computer so that the Recovery policy configured for this system contains invalid recovery certificate message does not prevent you from using the Encrypting File System is a bit tricky and involves a number of steps, but we hope this guide can help you in this effort.
Login as an administrator
First, log into your computer using the built-in Administrator account. Logging into your computer running Windows Vista using another account with administrative privileges is known to cause issues when fixing this issue.
Create a file recovery certificate
Second, create a recovery certificate for encrypted files. You can do this by executing the following steps
Start menu
Run
Cmd
(this can be accessed also through Start -> All Programs -> Accessories -> Command Prompt)
Type cipher /r:recovery_certificate and hit Enter
Type a strong password. This will be your password to your data; it is advised to use at least 10 characters, a combination of lower and upper case, numbers and special characters.
The print screen above shows how to generate a recovery certificate. The certificate is stored in a file called recovery_certificate.CER located in the directory shown at the command prompt. Note: It is a good idea to move this file to an encrypted USB disk and store the media in a safe. This file will be your key to your data.
Install file recovery certificate (Data Recovery Agent)
The next step is to let the system know about your file recovery certificate by generating so called Data Recovery Agent.
Start menu
Run
Type gpedit.msc and hit Enter to run the Group Policy editor
Navigate to the
-> Local Computer Policy
-> Computer Configuration
-> Windows Settings
-> Security Settings
->Public Key Policies
-> right click Encrypting File System
-> and select Add Data Recovery Agent
Follow the wizard and when it asks you for a file with the certificate, browse to the folder containing the recovery_certificate.CER file which you created earlier and select that file.
Update policies
The next step is to update policies by going to the command prompt and executing the gpupdate /force command.
This did not help – what else should I do?
In some cases, people ran into situations when this solution did not work, or in other words, they were getting the Recovery policy configured for this system contains invalid recovery certificate message even after adding the recovery certificate to the policies. The following are a few additional steps to check.
Delete old certificates
The Encrypting File System screen in the Group Policy editor should list only one Data Recovery Agent (certificate). If you see more than one Data Recovery Agent there, then export them first and delete all but the one with the farthest expiration date.
Delete certificates from certificate stores
Open the certificates Microsoft Management Console snap-in (type mmc in the Start -> Run screen and hit Enter, then go to File -> Add/Remove Snap In and select Certificates from the Available Snap-ins menu, then hit Add and select My user account). Navigate to the following location:
-> Console Root
-> Certificates – current user
-> Personal
-> Certificates
and make sure the right pane shows no File Recovery certificates. If it does show any, then export and delete them.
Check applicable policies and determine used certificates
Go to the Start menu
Run
Type rsop.msc and hit Enter to run the Resultant Set of Policy tool
Navigate to the
-> Computer Configuration
-> Windows Settings
-> Security Settings
-> Public Key Policies
-> Encrypted File System
The right pane should list the defining recovery agent and show its expiration date as well. By default, there should be a certificate given to the Administrator account. If there is no valid certificate or the certificate is expired, the encryption feature will not work and you will see the Recovery policy configured for this system contains invalid recovery certificate message because a valid and unexpired recovery is required for the Encrypting File System to work.
Update certificates
Open the command prompt and run the cipher /u command. This will update previously encrypted files with the new recovery certificate.
Log in as the Administrator
All the steps described on this page need to be executed under the default Administrator account.
Invalid recovery certificate and other issues
Everything about invalid recovery certificate has been said on this web page, but you might find some other articles handy for other issues.
Posted in Silverlight
Leave a comment
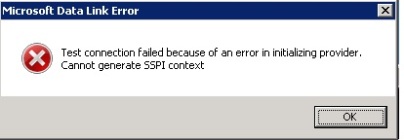
Using SPN tool to bypass SQL UDL Connection Test Cannot generate SSPI context error.
If the UDL connection refused and prompt an error as shown below
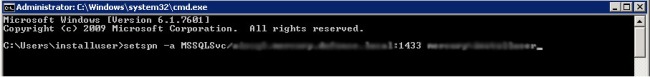
We have to register SQL with the account name: “<domain>\user” with the help of SPN (Service Principal Name) tool. The SPN is a unique idendifier for each service that is running on servers. It is essentially a mapping between a principal name and the Windows account that started the server instance service. This is needed because the client will use the server’s hostname and the TCP/IP port to which it connects to compose an SPN. If the SPN mapping has not been performed, then the Windows security layer will be unable to determine the account associated with the SPN. To register the SPN syntax is;
setspn –A MSSQLSvc/<servername>.<domainname>:<port> accountname
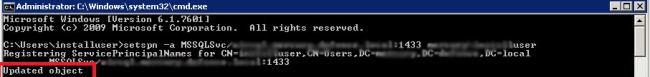
Open a command window with run as administrator and write as shown below and click “Enter”.
The result must be “Updated object” as shown below
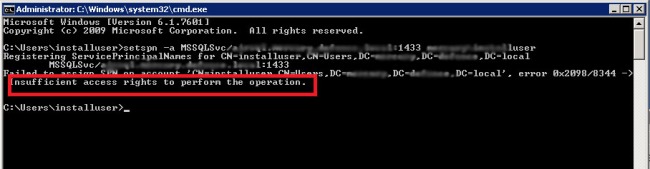
Re-test UDL connection.
If you get an error; “Insufficient access rights to perform the operation.” As shown below, please follow the steps on DC server.
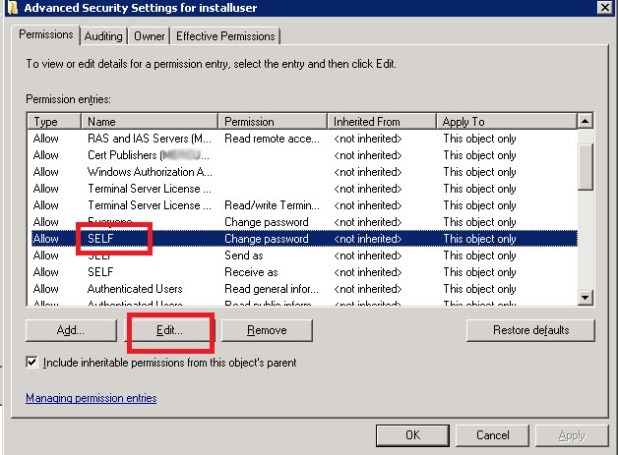
Go to DC Server or contact your system administrator if you have no access to it to give “Read servicePrincipalName” and “Write servicePrincipleName” permission to installuser as described below steps
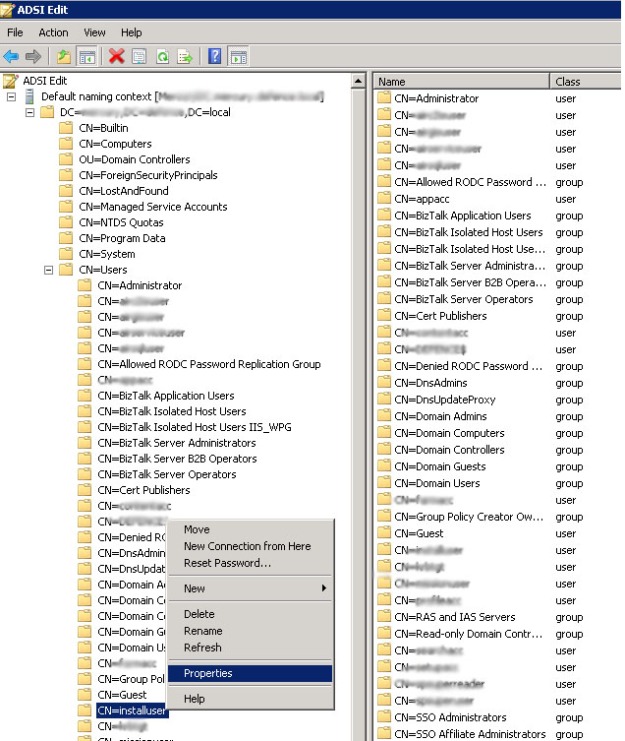
Click Start, click Run, type Adsiedit.msc, and then click OK
In the ADSI Edit snap-in, expand Domain [DomainName], expand DC= RootDomainName, expand CN=Users, right-click CN= AccountName , and then click Properties.
Notes
– DomainName is a placeholder for the name of the domain.
– RootDomainName is a placeholder for the name of the root domain.
– AccountName is a placeholder for the account that you specify to start the SQL Server service.
– If you specify the Local System account to start the SQL Server service, AccountName is a placeholder for the account that you use to log on to Microsoft Windows.
– If you specify a domain user account to start the SQL Server service, AccountName is a placeholder for the domain user account.
In the CN= AccountName Properties dialog box, click the Security tab.
On the Security tab, click Advanced.
In the Advanced Security Settings dialog box, make sure that SELF is listed under Permission entries. (If SELF is not listed, click Add, and then add SELF.)
Under Permission entries, click SELF, and then click Edit.
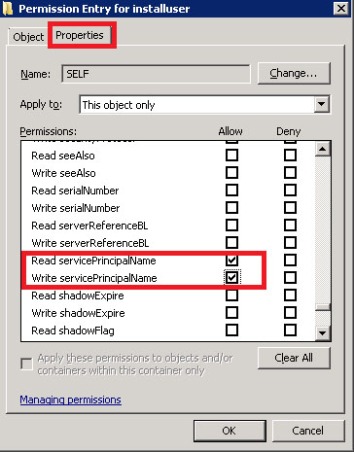
In the Permission Entry dialog box, click the Properties tab.
On the Properties tab, click This object only in the Apply onto list, and then click to select the check boxes for the following permissions under Permissions:
– Read servicePrincipalName
– Write servicePrincipalName
Click OK three times.
Close ADSI edit and go to your server where UDL has been created.
Re-test UDL connection
Visual Studio 2012 with Small(non-capital) Menu
Change registry
HKEY_CURRENT_USER\Software\Microsoft\VisualStudio\11.0\General\SuppressUppercaseConversion
OR
Run below line at powershell
Set-ItemProperty -Path HKCU:\Software\Microsoft\VisualStudio\11.0\General -Name SuppressUppercaseConversion -Type DWord -Value 1
Posted in Visual Studio
Leave a comment